COMPLIMENTARY TOOL
The Phishing Simulation Service
Discover how your employees would respond to a targeted email attack
- without any of the real world consequences.


Test Your Company's Detection Skills
When a phishing attack campaign manages to bypass existing email protections, the only layer of defence remaining is your own employees.
If it came down to it, would your employees rise to the challenge and serve as a human firewall, or would they inadvertently open the door to attackers?
With The Phishing Simulation Service you can gather valuable insights that will help you to identify vulnerabilities such as how many employees would click on a link in a suspicious email, or how many would actually report it to your IT team.
Combat Account Takeover
Account takeover is an incredibly dangerous threat because it may only take one compromise to impact your entire network.
This is because attackers will often infiltrate one primary account, and then leverage this to launch a lateral phishing campaign; targeting the remaining users within the network with a genuine, trustworthy email address that security solutions will not scrutinise.
The Phishing Simulation Service includes a relevant landing page linked to whichever email template you select, mimicking the spoofed login screens used by cyber criminals in these campaigns so you can evaluate how susceptible your organisation may be to account takeover.

The Simulation Service in 3 Simple Steps
For a more detailed explanation of the step-by-step process, read the datasheet here.
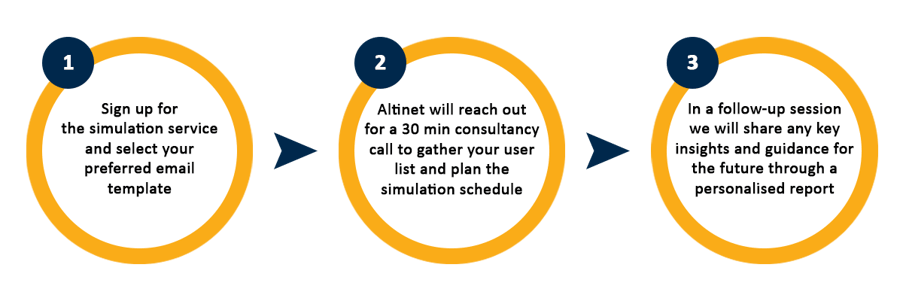
Sign up for The Phishing Simulation Service!
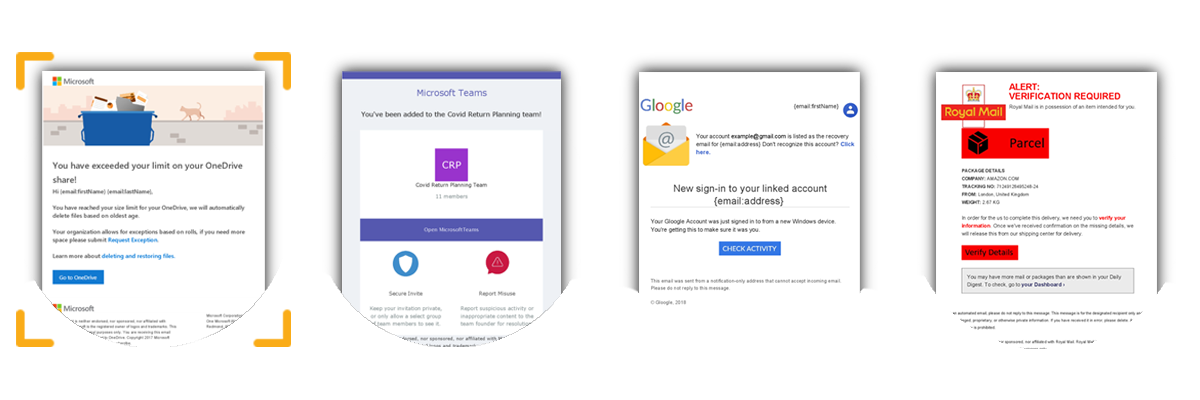
|
TEMPLATE 1 Microsoft OneDrive [ Most popular choice ] |
TEMPLATE 2 Microsoft Teams
|
TEMPLATE 3 Gmail |
TEMPLATE 4 Royal Mail
|